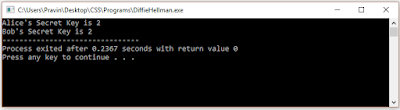
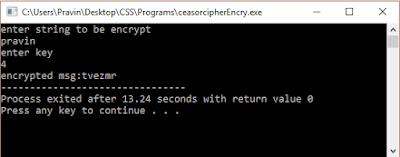
Blockchain
in social networking
Introduction to Blockchain
Technology
Blockchain is normally associated with Bitcoin
and other cryptocurrencies, but it is efficiently a database that’s
authenticated by a wider community, rather than a middle authority. It’s a
collection of records that a crowd oversees and maintains, rather than relying
on a single entity, which most expected hosts data on a particular server. Of
course, a physical database kept on paper could never be supervised by tens of
thousands of peers. That’s where computers, and the internet, come in. Each
“block” stands for a number of transactional records, and the “chain” component
links them all together with a hash function. As records are shaped, they are
established by a distributed network of computers and paired up with the
preceding entry in the chain, thereby generating a chain of blocks or a
Blockchain.
Blockchain Risks and
Opportunities
Opportunities:
The potential opportunities of blockchain
technology will be examined in this article under three broad categories as
follows:
1. Commerce
The first recognizable niche that comes to
mind when the blockchain is mentioned is commerce. The first ever successful
implementation of the blockchain framework resulted in Bitcoin, a payment
processing architecture. This, and the fact that the majority of the blockchain
applications that have been launched since then have been focused on
cryptocurrencies has led some to believe that crypto is all there is to
blockchains.
The entire framework of global commerce
presents a veritable opportunity for blockchain implementation. Blockchain
technology can be applied to almost every aspect of commerce. One of the most
valuable opportunity for blockchain adoption in commerce is the area of
cross-border transactions. The current framework for cross-border transactions
is one that involves a number of processes and checks that slow down the
transactions and even make them quite expensive. Blockchain technology has the
potential to create a borderless network architecture that will enable
cross-border transactions to happen almost instantaneously.
2. Government
Government is charged with a whole host of
duties and responsibilities that must be discharged for the benefit of the
citizens. Blockchain technology has a vital role to play in government
especially in the context of the 21st-century world. Blockchains can be
utilized for identity management systems, document processing, safeguarding
financial and state services, as well as transmitting sensitive information
just to mention a few.
Risks:
The blockchain risks can be broadly classified
under three categories:
Standard risks:
Blockchain technologies expose institutions to
risks that are similar to those associated with current business processes but
introduce nuances for which entities need to account.
Value transfer risks:
Blockchain enables peer-to-peer transfer of
value without the need for a central intermediary. The value transferred could
be assets, identity, or information. This new business model exposes the
interacting parties to new risks that were previously managed by central
intermediaries.
Smart contract risks:
Smart contracts can potentially encode complex
business, financial, and legal arrangements on the blockchain, and could result
in the risk associated with the one-to-one mapping of these arrangements from
the physical to the digital framework.
Key challenges
One of the challenges of blockchain is in its
very nature: the distributed ledger. Because every endpoint has to have a copy
of the entire blockchain, and that blockchain is constantly growing as more
things are added, the system gets slower, taking up more space. If the same
sort of system was implemented under a medical records system, you can see
where it would become untenable very quickly.
The biggest challenge of blockchain is the
lack of awareness of the technology, and the lack of understanding how it
works.
Case study
Blockchain in social networking:
Whether you are a social media marketer the one who is offering services
to businesses or a business owner who is making use of social media to reach
customers, it is quite important that you understand that social media is about
to go through a striking shift.
The blockchain is unsettling a number of industries, and social media is
among those which is likely to feel the ramifications of blockchain disruption
first. Companies actually used to create their brands on platforms like
Facebook and Twitter are about to realize that all that investment of time may
have been for nought. As it is going to change the platforms consumers and
businesses use and how they network, social media marketing will go through a
disturbance which they never expected and even it never did before.
Problems Identified
1. Control over data
Social network users currently have no control over their data. Once a
user has an account on a social network it is as if they relinquish their right
to their personal information and control over content. Total control is in the
hands of social network owners who dictate what is to be viewed by users and
what is not. And with such control, the social network platform owners are able
to profit from their users without the users’ consent.
2. Privacy
If the recent Facebook data breach is anything to go by, then the
current social networks are proving to have poor security. Users are
susceptible to attacks which are known to expose their personal information.
3. Single Point of Failure
Because of their centralized nature, conventional social networks are
vulnerable to attacks that often lead to costly losses. Hackers only have one
point of attack, which ones breached they can get access to a flood of users’
information. For example, in 2012 a hacker broke into LinkedIn network and got
away with some 6.5 million encrypted passwords and posted them on a Russian
hacker forum. Four years later another hacker who goes by the name Peace was
selling more of LinkedIn hacked user information. He claimed that the total
count of data stolen from LinkedIn reached 167 million and not 6.5 million as
thought before. Of which 117 million had both email and encrypted passwords.
Solutions Provided
Blockchain technology is the long-awaited cure to issues affecting the
current breed of social networks. The following features are what make
Blockchain technology so groundbreaking.
1. Transparency
Blockchain distributed nature eliminates the control of platforms by a
single entity. And since every transaction on the Blockchain-based platform is
tracked and audited by several servers and developers, it becomes impossible
for anyone to tamper with the data.
2. Control over data
By eliminating intermediaries, users on decentralized social networks
will own and control their data. Blockchain technology ensures that whatever
you post on the social network can be traced anywhere it goes and never be
duplicated. And the best part is that if you delete it, it is deleted in the
whole system and no unauthorized third parties can access and benefit from it.
3. Relevant content
Once control of your social network platforms is in your hands, you get
to dictate the type of content you would like to see. Therefore you don’t get
unwanted advertisements on your platforms that only benefit the advertisers and
not you.
4. Earning from social media
activity
Blockchain-based platforms enable you and your viewers, listeners,
readers, depending on the content you create, to build a direct relationship
that is monetarily beneficial to you.
Market Competition
As we are entering an era of change, a global phenomenon will soon
emerge as philosophies and beliefs shift and unexposed cultures experience new
technologies. In 20-30 years from now we are going to enter into a super
economy, where the content is much more equally distributed between the global
populations.
Right now the margins of distribution are narrow, and this is about to
change. This is disruptive change that can happen overnight. People will be
able to buy essential products, solar panels, mobile phones, etc. This could
change markets on a global scale as disadvantaged populations can more easily
communicate.
Kodak was liquidated overnight when Nokia chose to ship their mobile
phones with cameras. The same could happen with social media and the banking
system. This could herald a sea change in global economics. Only one single
form of social media has to accommodate micro-payments in order for this to
happen. Once they integrate with the Blockchain, then boom! Something big is
happening. From there it will spread like wildfire. There will be a big change
in the landscape of social media companies. The first to leap will gain the
most traction, then the others must also conform or die. Social media companies
will have no justification to exist if they do not get onboard.
The next question is what will happen to all the advertisers on social
media? Revenues of companies that make money from advertisements (Google,
Yahoo, Facebook, etc.) will go down. There would be less justification to charge
your user base money for advertisements. Major businesses may be rendered
obsolete – this will be the next disruption of the chain. Social media products
may no longer be a necessary advertising platform. Existing companies will try
to ensure they are not outgrown when equivalent open source platforms rise
quickly and establish firm footings in fresh soil.
Future Trends
1) More earning
The combination of social networks and
cryptocurrencies enabled with blockchain development is another tempting example
of the future of social platforms. When decentralized platforms become common,
users of social networks will have the option of choosing the platforms on
which to establish a network.
The ability to earn small amounts of cryptocurrencies for their
activities will attract users to platforms where contributions to platform
growth are rewarded. Think about how much time you spend currently on social
networking sites like Twitter and Facebook and imagine if each publication you
won earned you a small amount of Bitcoin. A future of social networks enabled
for encryption is really intriguing.
2) No more spams
Smart contracts and blockchain development
technology will also influence the dissemination of false content. The current
social media networks are flooded with everything from false news to spam bots.
In the social media networks of the future, the distribution of content will be
based on verified information and the propagation of traceable data. The
ability to block content and its collaborators is a tempting option for brand
creators.
3) No fraudulent impressions
There will be a growing interest in identities
verified online. With massive bot issues on social media platforms such as
Facebook and Twitter, business owners are increasingly looking for reaching
reliable platforms for their customers where they can increase their marketing
ROI.